Phishing emails are one the biggest security threads at the moment. The phishing emails are getting better every year making it hard to block them up front. Typically users find them also hard to recognize and click too often on the links in the emails. We can prevent that by adding an external email warning or tag external emails.
There are basically two options, which you should both implement. The first one is enabling the external email tag in Exchange Online. This will enable a built-in warning between the subject and body of the email when the email is sent from outside your organization.
The second option is to add a custom warning banner at the top of the email. We can show the custom warning based on words in the subject or body, making it really versatile. It allows us to show a warning for phrases like, “keep your password”, or “update your password”
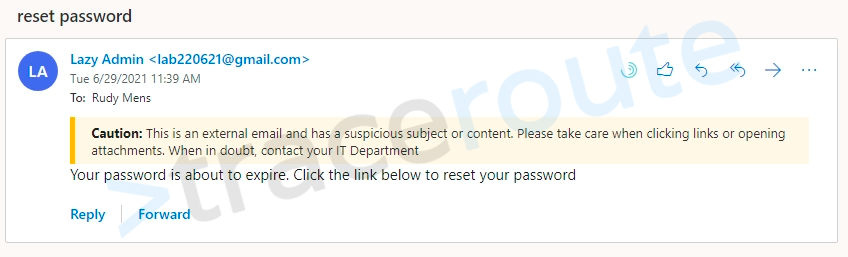
In this article, I will explain how you can enable the Exchange Online External Tag and create custom external email warnings in Office 365 and Outlook.
Enable External Email Tag
External email tagging is an extra security layer to help protect you against phishing emails. Features like SPF, DKIM, and DMARC already do a great job in preventing most phishing emails, but we all know that it’s still not enough.
Especially spoofed emails, which seem to have been sent from a trusted source in your organization, are a great security risk.
Microsoft recently launched a new feature in Exchange Online to help increase the user’s awareness by automatically tagging external emails. The external tag is supported in the following versions of Outlook:
- Outlook Online
- Outlook for Window – rollout started may 2021
- Outlook for Mac – Version 16.47 and higher
- Outlook Mobile App – iOS and Android – version 4.2111.0 and higher
How to Enable External Email Tagging
At the moment we can only enable external email tagging through PowerShell. Make sure you have the Exchange Online module installed before you start.
It can take up to 48 hours before the external tag will show up in Outlook. Only new emails will get tagged after you enabled the feature, existing emails won’t.
Step 1 – Connect to Exchange Online
The first step is to connect to Exchange Online.
1. Connect-ExchangeOnline -userPrincipalName john@contoso.com
Step 2 – Enable external tagging
The next step is to enable the external tagging in Exchange Online.
1. Set-ExternalInOutlook -Enabled $true
You can verify the settings with the following cmdlet:
1. Get-ExternalInOutlook
2.
3. # Result:
4. RunspaceId : 4b07eecc-34c5-4add-8ee4-80d25aa4aff4
5. Identity : 11e55098-68ad-4992-aaf8-c5fdceb3b6da
6. Enabled : True # < External tagging enabled
7. AllowList : {}
Step 3 – Add domains to allow list (optional)
It’s possible to exclude domains from the external tag. This can be useful if your organization has different tenants or work closely with specific partners.
By using the @{add=""} syntax we make sure that any existing domain in the list is preserved. Without it, all existing domains in the AllowList would be removed.
1. Set-ExternalInOutlook -AllowList @{Add="lazyadmin.nl", "lazydev.nl"}
To remove a single, or multiple, domains from the list you can use the following syntax
1. Set-ExternalInOutlook -AllowList @{Remove="lazyadmin.nl", "lazydev.nl"}
We can verify the settings with the following cmdlet
1. Get-ExternalInOutlook
2.
3. # Result
4. RunspaceId : 6468fcef-1cb9-4d6c-9cae-6b8dbc999971
5. Identity : 11e55098-68ad-4992-aaf8-c5fdceb3b6da
6. Enabled : True
7. AllowList : {lazyadmin.nl, lazydev.nl} # domains added to allow list
Tagging external emails in Outlook is a new feature in Microsoft Office 365. New features are always first rolled out to the insiders and targeted release tenants. If it’s doesn’t work after 48 hours or you want new features faster for your tenant, then make sure you change the Release Preferences in the Microsoft Office 365 Admin Center.

- Open the admin center
- Go to Settings > Org Settings
- Click on Organization profile and select Release Preferences
- Make sure that Targeted release for everyone is selected.
Create External Email Warning
External email warnings are custom messages that you can add to the top of the email. It’s still a good idea to warn your users of malicious emails, even though we can now tag external emails in Exchange Online. The custom warning allows us to warn users based on the content or subject of the email.
So we are not going to warn users for every single external email with this, only if the content or subject contains specific words or phrases.
To create the external email warning we are going to use Exchange Transport Rules. You can use this method both in Exchange Online and Exchange On-Premise.
Note: I have also created a script that will show a warning then users receive an external email with the same display name as a user of your organization (Impersonation). Read more about it in this article.
We are first going to use the Office 365 Exchange Online Admin Center to configure the external email warning. At the end of the article, I also have a PowerShell script that you can use.
Configure External Email Warning in Exchange Online
If you want to configure the external email warning for only a single-tenant, then it’s more convenient to use the Exchange Admin Center for this.
Step 1 – Create a new Mail Flow Rule in the Exchange Admin Center
– Login to the Exchange Admin Center
– Expand Mail flow
– Select Rules
– Click on the plus and select Create a new Rule

Step 2 – Give the rule a name
Enter a name for the rule so you can easily recognize it later, for example, “external email warning”
Step 3 – Configure Apply this rule if
We only want to apply the rule when the email comes from an external source. And we also want to add a filter to match the subject or body against a list of words.
- Click on Apply this rule if
- Choose The sender is located…
- Select Outside the organization
We need to add extra conditions, to do this you will need to click on More options…

With more options enabled we can now add extra conditions to the Apply this rule if conditions.
- Click on Add Condition under Apply this rule if
- Choose The recipient is located...
- Select Inside this organization

We are going to add one more condition so we only show the warning when the subject or body matches specific words or phrases:
- Click on Add Condition under Apply this rule if
- Choose The subject or body matches…
- Select Specific words or phrases.
Now you can add all words and phrases manually or use PowerShell for this. Just add one or two phrases for now and we will update the list later with PowerShell.

The list below is based on the Regex list from SwiftOnSecurity that you can find here on GitHub.
1. Password.*[expire|reset] 2. Password access 3. [reset|change|update].*password 4. Change.*password 5. \.odt 6. E-Notification 7. EMERGENCY 8. Retrieve*.document 9. Download*.document 10. confirm ownership for 11. word must be installed 12. prevent further unauthorized 13. prevent further unauthorised 14. informations has been 15. fallow our process 16. confirm your informations 17. failed to validate 18. unable to verify 19. delayed payment 20. activate your account 21. Update your payment 22. submit your payment 23. via Paypal 24. has been compromised 25. FRAUD NOTICE 26. your account will be closed 27. your apple id was used to sign in to 28. was blocked for violation 29. urged to download 30. that you validate your account 31. multiple login attempt 32. trying to access your account 33. suspend your account 34. restricted if you fail to update 35. informations on your account 36. update your account information 37. update in our security 38. Unusual sign-in activity 39. Account Was Limited 40. verify and reactivate 41. has.*been.*limited 42. have.*locked 43. has.*been.*suspended 44. unusual.*activity 45. notifications.*pending 46. your\ (customer\ )?account\ has 47. your\ (customer\ )?account\ was 48. new.*voice(\ )?mail 49. Periodic.*Maintenance 50. refund.*not.*approved 51. account.*(is\ )?on.*hold 52. wire.*transfer 53. secure.*update 54. secure.*document 55. temporar(il)?y.*deactivated 56. verification.*required 57. blocked\ your?\ online 58. suspicious\ activit 59. securely*.onedrive 60. securely*.dropbox 61. securely*.google drive 62. view message 63. view attachment
Step 4 – Adding the external email warning
With the conditions in place, is the next step to add the warning that we want to display. We are going to add the external email warning example below. But you can customize it to your needs of course.
At the end of the article, I have added a couple of other examples for the warning message.

We can use some basic HTML to format the warning message:
1. <!-- Yellow caution banner --> 2. <table border=0 cellspacing=0 cellpadding=0 align="left" width="100%"> 3. <tr> 4. <!-- Remove the next line if you don't want the Yellow bar on the left side --> 5. <td style="background:#ffb900;padding:5pt 2pt 5pt 2pt"></td> 6. 7. <td width="100%" cellpadding="7px 6px 7px 15px" style="background:#fff8e5;padding:5pt 4pt 5pt 12pt;word-wrap:break-word"> 8. <div style="color:#222222;"> 9. <span style="color:#222; font-weight:bold;">Caution:</span> 10. This is an external email and has a suspicious subject or content. Please take care when clicking links or opening attachments. When in doubt, contact your IT Department 11. </div> 12. </td> 13. </tr> 14. </table> 15. <br />
- Click on Do the following
- Choose Apply a disclaimer to the message
- Select Prepend the disclaimer…
- Click on Enter text…
- Paste the HTML code from above into the text box
- Click on Select one.. and set the fallback action to Wrap

Step 5 – Add Exceptions
You might want to add some exceptions to the rule. You may have for example an application that sends emails with a password reset link. We can add multiple exceptions under Except if.
The exception can be based on domains, specific sender, words, IP Addresses, etc.
Step 6 – Save the rule
With the rule completed, you can save it to enable it. If you want to test the rule first you can change the Apply this rule if condition This Recipient is located to is this person and enter your own email address.
This way the rule will only be applied to your mailbox, allowing you to safely test it before rolling it out to the organization.
The complete rule should look similar to this:

Step 7 – Add all the words and phrases with PowerShell
The list of words and phrases is pretty long, so instead of adding them all manually, we are going to update the transport rule with PowerShell.
First, we need to get the transport rule based on its name. This is the same name we entered in step 2. If you are unsure, you can also list all the transport rules with Get-TransportRule
I always do a Get first to be sure that I have the correct rule before making any changes to the configuration of the rule.
1. # Connect to Exchange Online 2. # Enter your userprincipalname to use SSON 3. Connect-ExchangeOnline -userprincipalname john@contoso.com 4. 5. # Get the transport rule 6. Get-TransportRule -Identity "External Email Warning" | select -ExpandProperty SubjectOrBodyMatchesPatterns
This should return the rule that we have just created with the words or phrases that you entered manually in step 3.
I have saved the patterns in a text file in my temp folder. This way we can easily import it with PowerShell:
1. # Update the transport rule with all the patterns 2. Set-TransportRule -Identity "External Email Warning" -SubjectOrBodyMatchesPatterns (Get-Content C:\temp\patterns.txt) 3. 4. # Check if the import was successful: 5. Get-TransportRule -Identity "External Email Warning" | select -ExpandProperty SubjectOrBodyMatchesPatterns
Using PowerShell to create the External Warning
If you want to add the external email warning to multiple tenants, then it’s easier to use PowerShell. The script below creates an Exchange Online transport rule with all the settings as described earlier.
Make sure you have the patterns.txt in the same folder as the script.
1. # Connect to Exchange Online 2. Write-Host "Connect to Exchange Online" -ForegroundColor Cyan 3. Connect-ExchangeOnline 4. 5. $HTMLDisclaimer = '<table border=0 cellspacing=0 cellpadding=0 align="left" width="100%"> 6. <tr> 7. <td style="background:#ffb900;padding:5pt 2pt 5pt 2pt"></td> 8. <td width="100%" cellpadding="7px 6px 7px 15px" style="background:#fff8e5;padding:5pt 4pt 5pt 12pt;word-wrap:break-word"> 9. <div style="color:#222222;"> 10. <span style="color:#222; font-weight:bold;">Caution:</span> 11. This is an external email and has a suspicious subject or content. Please take care when clicking links or opening attachments. When in doubt, contact your IT Department 12. </div> 13. </td> 14. </tr> 15. </table> 16. <br/>' 17. 18. 19. Write-Host "Creating Transport Rule" -ForegroundColor Cyan 20. 21. # Create new Transport Rule 22. New-TransportRule -Name "External Email Warning" ` 23. -FromScope NotInOrganization ` 24. -SentToScope InOrganization ` 25. -SubjectOrBodyMatchesPatterns (Get-Content $PSScriptRoot\PhishingPatterns.txt) ` 26. -ApplyHtmlDisclaimerLocation Prepend ` 27. -ApplyHtmlDisclaimerText $HTMLDisclaimer ` 28. -ApplyHtmlDisclaimerFallbackAction Wrap 29. 30. Write-Host "Transport rule created" -ForegroundColor Green
You can also find the complete script, external email warning HTML code, and pattern list here in my GitHub Repository.
External Email Warning Examples
I have created a couple of external email warning examples that you can use. Some organizations maybe want a more prominent banner than others. These examples can be used directly or can help you with creating your own warning.
Make sure you leave the <br/> at the end of the warning banners. Because this will add an enter (white line) between the warning and the actual mail content.
Example 1 – Yellow warning banner

If you don’t like the dark yellow bar on the left side, then you can remove line 5 from the HTML code.
1. <!-- Yellow caution banner --> 2. <table border=0 cellspacing=0 cellpadding=0 align="left" width="100%"> 3. <tr> 4. <!-- Remove the next line if you don't want the Yellow bar on the left side --> 5. <td style="background:#ffb900;padding:5pt 2pt 5pt 2pt"></td> 6. 7. <td width="100%" cellpadding="7px 6px 7px 15px" style="background:#fff8e5;padding:5pt 4pt 5pt 12pt;word-wrap:break-word"> 8. <div style="color:#222222;"> 9. <span style="color:#222; font-weight:bold;">Caution:</span> 10. This is an external email and has a suspicious subject or content. Please take care when clicking links or opening attachments. When in doubt, contact your IT Department 11. </div> 12. </td> 13. </tr> 14. </table> 15. <br />
Example 2 – Blue information bar

The HTML code for this warning banner is:
1. <table border=0 cellspacing=0 cellpadding=0 align="left" width="100%"> 2. <tr> 3. <td style="background:#00A0d2;padding:5pt 2pt 5pt 2pt"></td> 4. <td width="100%" cellpadding="7px 6px 7px 15px" style="background:#e5f5fa;padding:5pt 4pt 5pt 12pt;word-wrap:break-word"> 5. <div style="color:#222222;"> 6. <span style="color:#222; font-weight:bold;">Caution:</span> 7. This is an external email and has a suspicious subject or content. Please take care when clicking links or opening attachments. When in doubt, contact your IT Department 8. </div> 9. </td> 10. </tr> 11. </table> 12. <br/>
Example 3 – White background warning

You can also use only a small red or dark yellow line in front of the warning.
1. <table border=0 cellspacing=0 cellpadding=0 align="left" width="100%"> 2. <tr> 3. <td style="background:#dc3232;padding:3pt 1pt 3pt 1pt"></td> 4. <td width="100%" cellpadding="3px 6px 3px 15px" style="background:#ffffff;padding:3pt 4pt 3pt 12pt;word-wrap:break-word"> 5. <div style="color:#222222;"> 6. <span style="color:#222; font-weight:bold;">Important:</span> 7. This is contains a suspicious subject or content. Do not click any link and do not open attachments unless you have confirmed the sender. 8. </div> 9. </td> 10. </tr> 11. </table> 12. <br />
Wrapping Up
I hope this article helped you with setting up your own external email warning. Make sure you enable the external email tag because this can really help you, users, with recognizing spoofed phishing mail earlier.
The custom external email warning that you can add to Office 365 and Outlook is really versatile. I don’t like to show the banner on every external email, because users will get too familiar with it, and it will lose its effect.
So by adding the extra conditions we make sure that only the mail with a high risk is flagged.
Make sure you also read this list with more than 18 security tips to protect your Office 365 tenant and check out this script for impersonation warning in Outlook. If you have any questions, just drop a comment below.

